Mastering Team Password Management: A Comprehensive Guide
Topics Covered
Today, effective team password management is crucial as we juggle more passwords, PINs, and credentials than we can remember, making a written list an insecure method of tracking them. Secure password sharing is vital for team-based collaboration, especially in this age of remote work. Businesses large and small need a robust team password management solution to safely create, protect, organize, and share access to online services, accounts, and applications as users come and go.
Passpack is a highly secure team password management application for businesses with employees, partners, and clients who need shared access to common digital resources. Passpack encourages good password hygiene to protect businesses from cyber threats that often start with a weak or compromised password. It offers a suite of tools designed to improve overall security while enhancing team-based collaboration.
But even the best security defenses can be circumvented if not implemented properly or rules are not enforced consistently. Passpack has been serving customers for over a decade, helping businesses maintain the integrity of their digital assets while providing secure access to necessary credentials.
Now we’d like to share some advice and best practices for team password management based on our years of industry experience. This article discusses several challenges and strategies for secure password sharing and policy implementation. We’ll review key technologies and capabilities any team password management solution under consideration should offer and point you to some related resources along the way.
Learn why businesses of every size need secure password sharing, and why the Passpack Password Management app should be your first line of defense against cyberattacks.
Why Shared Account Password Management?

In your personal life you keep your passwords to yourself. Who needs access to your bank, Netflix, or Facebook account but you? In a business setting, however, sharing passwords is necessary for team-based collaboration.
Multiple employees must access common resources and information such as customer databases, licensed applications, Google docs, OneDrive files, training materials, social media sites, bank accounts, and countless other critical digital assets to complete a project, assist a customer, update a patient record, or pay a bill, for example.
In team password management, understanding the risks and best practices for shared account password security is critical to safeguard sensitive information but also to streamline collaboration across teams, and ensure that everyone has the necessary access without compromising on security.
The challenge many IT managers face is how to control and monitor access to all the shared digital assets in a corporation so that all authorized users – and only authorized users – have access to the resources they need to do their jobs?
Shared account password management is defined as the use of the same credentials by multiple users to access company data.
In a business with multiple employees, it would simply be untenable to manage unique passwords for each user and every resource. Think of the drain on IT resources just to reset forgotten passwords, plus the lost productivity while users wait for re-authorization.
As employees come and go, it would be impossible to guarantee the security of company data against breaches without constantly resetting everyone’s credentials.
Now add in the multitude of outside partners, suppliers, sales reps, and others who need access to company systems and the attack surface is multiplied – especially if these people create and manage their own passwords without any guardrails.
Team password management resolves the issues of password overload for employees and lightens IT’s burden of resetting them. For instance, all members of the accounts payable team – and only the accounts payable team – access the company bank account using the same credentials. They can cover for each other in the event of absence or vacation, pitch in and split workloads during peak periods, and handle any vendor inquiry. But it’s not without its risks.
Risks of Insecure Password Sharing
Left to their own devices, users may pick up some bad habits that make passwords easier to remember but could lead to potential security breaches. We call that poor password hygiene.
- Use of weak or easily compromised passwords, like a birthday or pet name
- Use of the same character string for multiple accounts
- Using slight variations of a root password for different accounts
- Recycling old or expired passwords
- Keeping a written list or storing them in an unprotected web browser
- Sharing passwords by writing them down on a sticky note
- Sharing passwords by repeating them aloud for everyone in earshot to hear
Should a breach occur because of a compromised password, there will be no visibility into who is responsible. Data may be stolen, corrupted, or held for ransom. If your company operates in a regulated industry like financial services or healthcare, there’s going to be fines to pay and reputation damage.
Yet businesses of every size continue to practice shared passwords for common digital resources because, well, they have no choice. But they need to be able to control it.
Passpack Optimizes Shared Account Password Management
To minimize the risks of sharing passwords within an organization, a centralized shared account password management application is required.
Designed around the concept of centralized administrator control, all requests for creating and changing passwords, invitations to a new digital resource, adding new users and deleting departing employees flow through a designated password administrator. Passpack gives an organization total control and 360° visibility over all password-related activity and every user.
Passpack reduces a company’s risk of exposure to a breach by setting rules and creating secure workflows for the creation, sharing, and management of passwords across an entire organization:
- Unlimited users, passwords, and discreet teams
- Password generator to create strong credentials
- Zero-knowledge architecture
- User-defined Packing Key for added security
- End-to-end password encryption
- Create policies for password variations, expirations, and recycling
We’ll dig into the details of these capabilities and more, next.
Building a Team Password Management Policy

Many people have predicted that passkeys and biometrics will eventually replace the traditional password because of all its inherent insecurities. They may be right. Especially since hackers have gotten better at cracking them and phishing attempts are harder to spot.
“Passwordless” access for personal use is here, like when you use your fingerprint or facial recognition to open your phone or launch an app. But it remains to be seen how businesses can use an individual’s unique data as a shared credential for multiple employees to access the same digital resource.
In the meantime, passwords remain most business’ first line of defense for information security and privacy. Until a proven password replacement for business use arrives, the best course of action is to formalize your company’s employee password management policy to eliminate the vulnerabilities of weak passwords and poor password hygiene.
A Good Team Password Management Solution Is the Foundation for A Strong Overall Cyber Defense
Step One: Implement a modern team password management application like Passpack to provide the tools, rules, and enforce consistent password creation and sharing policies across the entire organization. Passpack solves for the insecurities of allowing each employee to create and manage their own credentials and having multiple passwords to unlock the same asset.
A strong team password management policy defines how passwords are created, stored, used, and shared, and will also:
- Centralize administrative tasks for complete visibility into all password-related activities
- Protect passwords in transit and at rest with end-to-end data encryption
- Offer a password generator tool to create strong passwords
- Track password activity in the event of a breach
- Disallow the use of aged, weak, or recycled passwords
- Speed employee on/off boarding without impacting access of other team members
The types of information and systems that should be password protected from a breach in a business include:
- Intellectual property and proprietary digital assets
- Communications and social media accounts
- Network and software applications/licenses
- Confidential business plans and go-to-market strategies
- Customer or patient data
- Bank account and credit card numbers, and financial reporting information
When the passwords to these and other business assets are shared carelessly a business opens itself up to:
- Malware and ransomware attacks
- Denial of service (DoS) attacks
- Lost or stolen customer data
- Theft of digital assets
- Reputational damage and loss of business
- Fines and penalties for compliance violation
Best Practices for Team Password Management Policy & Sharing
To mitigate these risks and shore up overall security at your business, your employee password management policy should incorporate these best practices:
- Never store passwords as plain text in written form
- Do not store passwords in browsers
- Limit password access to those on a need-to-know basis
- Do not allow employees to recycle old passwords
- Use multi-factor authentication (MFA)
- Use Single Sign On (SSO) technology in larger organizations
- Set a maximum number of account login attempts before the system automatically locks out the user
- Set time limits to automatically logout employees from a password-protected account after a designated period of inactivity
- Immediately suspend access to former employees
- Delete inactive accounts
- Change passwords to shared accounts when a team member leaves the organization
- Use different passwords for every account
- Train employees to alert IT if they suspect an account has been compromised
- Prevent staff from accessing company servers using public computers, only allowing logins from trusted IP addresses (IP Whitelisting)
One last point: Password manager applications are a natural target for cybercriminals, as one successful attack on the app provides access to all stored passwords. The password manager application itself must be highly secured. Make sure the solution you choose is built on Zero Knowledge System Architecture, like Passpack, to eliminate the threat of a breach to the application.
Unlocking the Power of Team Password Sharing
We’ve made our point. Let’s assume we’ve convinced you to create a company-wide employee password management policy and install a password manager app to help insulate your company against cyberthreats and breaches. What are you going to do with it?
The password manager app serves as more than just a central repository for all company passwords, PINs, and credentials; it also enables the missing element necessary to take control of shared account password management between trusted users.
When you’re a sole professional you make your own rules for password length and strength, change them whenever you want, and you never have to tell anyone. You trust yourself. When you’re part of a team, however, then it’s not just about you anymore. Your coworkers and employees need access to different resources to their jobs.
With a password manager app, you can assign a single credential to unlock an account, app, website, or digital service and create a team of users authorized to access the credential to open the resource.
Divide and Conquer Security Vulnerabilities
Not every employee needs access to every resource, so you need the ability to create multiple discreet teams of users by responsibility. For example:
- Members of the sales team need access to the CRM app, customer database, and inventory and ordering systems. But they don’t need…
- Access to documents and files stored on Google Drive or iCloud, and apps like MS Office, the Adobe Suite, Zoom, and Slack for the engineering and production teams to collaborate. But these teams don’t get access to…
- The social media passwords the marketing team uses to constantly pop in and out of the company website and to post to LinkedIn, Facebook, and Instagram. But they can’t access…
- The personnel and payroll files of employees in the Human Resources department, who do not have access to…
- The network settings, data storage, and infrastructure assets managed by the IT team, who have no reason to see…
- Bank account numbers and other company financial assets managed by the executive or administrative teams.
You need a password sharing tool to foster teamwork and collaboration among multiple teams; one that ensures employees have access to the resources they need, and only those resources. You need Passpack.
Passpack utilizes military-grade AES-256 encryption for data security and incorporates advanced capabilities including secure password generation, access, management, and sharing to allow IT managers and employees to access critical information and applications swiftly and securely.
Passpack includes its own password generator tool that allows businesses to set the minimum thresholds all employees must follow for character string length and strength, the use of special symbols or numbers, rules for password sharing and recycling, and schedules for credential expiration or rotation periods. Passpack will not allow the use of passwords below the minimum level of difficulty set by the administrator.
Passpack eliminates the need for written lists, securely shares passwords, speeds employee on- and off-boarding, and monitors individual user activity and histories to provide traceability in the event of a breach. Here’s how it works:
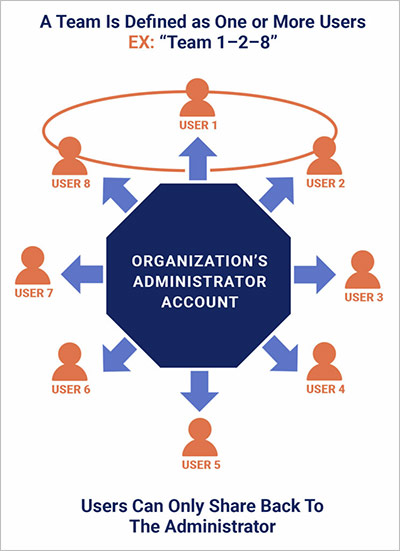 Passpack is designed around the concept of centralized administrator control. That means all requests for creating and modifying passwords, changing user permissions, sending invitations to a new digital resource, adding new users and deleting departing employees all must pass through a designated password administrator account. This person grants access to users and has visibility into every user’s activity. Users do not have access to other passwords that are not shared within their Team.
Passpack is designed around the concept of centralized administrator control. That means all requests for creating and modifying passwords, changing user permissions, sending invitations to a new digital resource, adding new users and deleting departing employees all must pass through a designated password administrator account. This person grants access to users and has visibility into every user’s activity. Users do not have access to other passwords that are not shared within their Team.
Should a user create a password for a new resource or request access to an existing one, the password can only be shared with the administrator account; the admin must then re-share the password out to other members of the team. Passwords are encrypted end-to-end during transmission. It can only be decrypted on the user’s device, meaning passwords are safe while in transit and at rest.
This is how Passpack enables organizations to retain centralized control and total visibility over all company passwords. User-level controls allow admins to easily change individual access rights without affecting other team members for fast and easy employee on/off boarding.
The Benefits of a Zero-Knowledge Password Manager
A Google search will return over 70 commercially available team password management software applications. Which one is right for your business?
There are free password managers and those available as paid subscriptions. There are solutions targeted at personal use, SMBs, and large enterprises. Some are platform-agnostic, others are optimized for specific devices, web browsers, or operating systems.
They all essentially do the same thing: keep your passwords safe and secure. It is how the app does it that should be of utmost importance to you. Because nowadays, anything can be hacked.
The first thing you should be looking for in a team password management app for use in a team-based business environment is a Zero-Knowledge Password Manager. This is a must-have, and if the app you are considering doesn’t use it, keep looking.
The primary reason for a zero-knowledge password manager is that even if a user’s device is lost, stolen, or hacked, there is no way to access the data stored in it.
The best password manager applications are built on a zero-knowledge architecture and all the biggest and well-known names in the market use it, including Passpack. But there are different ways to implement it.
The Unmatched Strength of Passpack’s Zero-Knowledge Password Management
Basically, zero-knowledge architecture means only you know what is stored in your vault and how to access it. When sharing access with another, it allows a user to prove they have authorization to a resource without revealing the key, only that the key matches.
Some identity and access management (IAM) providers have customers set up their accounts with a master username and a password that also doubles as the account’s encryption key for convenience, but this method opens a security loophole: If the master password is ever compromised, so is the encryption key, and all account data is exposed.
Passpack’s implementation of zero-knowledge architecture requires the use of an encryption key that is completely separate from the username and password. Called the Packing Key, it adds another step, and another critical layer of security.
The Packing Key uses AES-256 encryption, is known only to the end-user, and must be entered each time to unlock passwords and other confidential information (also AES-256 encrypted) stored in their Passpack account.
Further, the Packing Key is never made available to Passpack, its employees, or outside parties. End-users are the only ones who know their Packing Key.
Should Passpack ever be hacked, (unlikely, but never say never) your data remains safe because we’ve never seen anything other than your minimal login information (also encrypted) and your account’s login history. Passpack has no knowledge of any content – there’s nothing for hackers to steal.
Should a user’s device be lost or stolen, all password-related data remains inaccessible, protected by the Packing Key.
When it comes to peace of mind, nothing beats Passpack’s Zero-Knowledge Password Manager.
Single Sign-On (SSO) Team Password Management
This is a topic usually of interest to enterprises with large employee populations. But if your company has its eyes on growth, already uses multiple networked systems, applications, and websites, or has employees complaining of password fatigue, read on.
What is SSO?
SSO simplifies team password management and reduces password fatigue by assigning one set of credentials to each employee, unlocking the power of SSO passwords.
For end-users SSO is about convenience. It eliminates the need for employees to create, remember, and update unique passwords for what could be dozens of accounts. SSO boosts employee productivity by simplifying access to digital resources without having to log in and out of each one.
For businesses, SSO eliminates manual password provisioning tasks, reduces administrative burdens, and facilitates quick on- and off-boarding when employees come and go. It enforces the use of stronger passwords and better security policies through centralized control. SSO tracks user activity for compliance purposes, and can identify the source in the event of a breach.
When logging into the company network, an employee using their SSO identity instantly sees a personalized dashboard of all digital resources to which they are granted permission to use. No further authentication is required.
SSO usually requires the use of a third-party IAM provider such as Google, Microsoft Azure, Okta, and OneLogin to validate user credentials. This provides an extra layer of security by validating trusted user credentials against a master database outside the customer’s network environment.
But SSO by itself is not without risks. If the SSO provider goes down, access to all connected sites is halted. If one user’s master credentials are compromised, then every account and system accessible to that employee is vulnerable. Further, there are resources SSO does not support, and highly sensitive credentials to bank accounts and C-suite files for which SSO simply should not be used.
The Passpack + SSO Solution
The best course of action is to implement SSO in tandem with a password manager like Passpack. This way, users have a single outward-facing identity for fast and convenient access, coupled with strong password protection and credential management for individual user accounts.
Now, when a user logs in to the company network using their SSO identity, Passpack appears as one of the digital resources presented to users, along with any other password-protected assets authorized for that user. The credentials to more sensitive assets like customer data, bank accounts, ERP applications, and other privileged web services remain protected in the Passpack vault behind the user’s Packing Key.
Passpack currently supports the Google SSO standard, with plans to release SSO password management for Microsoft Azure shortly. This will position Passpack to support the team password management needs of most any business using SSO.
The Importance of Multi-factor Authentication (MFA)
Multi-factor authentication (MFA), sometimes called Two-Factor Authentication (TFA) is a multi-step account login process that requires users to enter more information than just a password. It makes you prove you’re who you say you are for an added layer of security.
MFA is a simple and easy method for small business to increase security.
MFA uses two or more pieces of separate data to undeniably confirm user identity:
- Something a user knows in addition to the password, like a preexisting PIN, answering a secret question, or being asked to enter a one-time code sent to their email or as a text message
- Something a user has, like a mobile phone, an email account, smart card, key fob, or a YubiKey USB stick
- Something a user is, like a unique biometric attribute such as a fingerprint, facial recognition, or retina scan
Access is granted only after the authentication sequence is completed and the system verifies that all pieces of evidence are from the same user.
Multi-factor authentication minimizes access risks due to human error, lost devices, or forgotten passwords. With MFA in place, organizations can conduct online activities with added confidence, knowing only twice verified (or more) users can access digital resources.
Additionally, MFA systems can be configured to send alerts when it detects suspicious login attempts as another warning against cyberattacks.
Passpack supports two widely used MFA services, Google Authenticator and Microsoft Authenticator, plus the use of physical YubiKeys. You must download the authenticator app for your platform from the proper online app store. Please note that using SMS text messaging as a token for MFA is not secure and is not recommended.
Get step-by-step instructions for Setting Up Two-Factor Authentication for Google Authenticator in Passpack, including emergency code access.
A YubiKey is a hardware authentication device with unique access codes stored within them. Instead of entering a password, the user presses a button on the YubiKey or inserts it into a USB port in a PC and an authentication code is transmitted to complete the login process.
Activating MFA while keeping all credentials securely stored in the Passpack vault is a robust solution for protecting your business from malware and ransomware attacks that often begin with poor password hygiene.
Identity & Access Management Starts with Passpack
Team Password management is a crucial component of the overall IAM ecosystem. The Passpack password management application supports best practices and supplies the tools to enhance your business’ security posture.
In addition to offering a password generation tool that enables companies to implement and enforce consistent password creation and management policies, Passpack supports SSO, MFA, and makes it easy to segment users by role and create a layered approach to security.
Passpack is built on a centralized model in which a single administrator has 100% control and visibility into all password-related activities across the organization. Passpack employs a zero-trust architecture and uses unique Packing Key technology. When sharing passwords among team members, all requests and communications pass through the admin for a closed loop, using end-to-end encryption so data is safe while in transit and at rest and never exposed to hackers.
When it comes to IAM, there is no single solution. Most organizations stitch together a combination of products from firewalls to malware detection to create their security blanket. Passpack plays a critical role in the user authentication facet of IAM for the secure creation, management, and sharing of digital credentials, enhancing business security from the ground up. Make Passpack your first line of defense against cyberthreats. It’s the best value in security for small to medium-size businesses
Unlock The Power of Team Password Management with Passpack
We offer versatile plans and tiers for businesses of every size at a fraction of the cost of competitive services. Visit us at www.passpack.com and try our service risk-free for 28 days and see how easy and affordable it is to keep all your passwords safe with Passpack.
Sources & Acknowledgements:
1infosecurity group, https://www.infosecurity-magazine.com/opinions/why-the-password-is-not-dead/, 6/20222Cybercrime Magazine, https://cybersecurityventures.com/60-percent-of-small-companies-close-within-6-months-of-being-hacked/, 1/2019
3PropertyCasulty360.com, https://www.propertycasualty360.com/2021/09/27/how-why-small-businesses-are-targeted-by-cybercriminals/?slreturn=20221107133204, 9/2021
4BBC News, https://www.bbc.com/news/business-63260648, 11/2022